Real-time Network Threat Detection
Monitor network traffic, detect intrusions, and receive actionable alerts to help you investigate and respond quickly.
Intrusion Detection & Monitoring System
We provide continuous monitoring of network traffic to identify malicious activity and suspicious behavior in real time.
Our dashboards surface attack trends, top targets, and detailed logs so security teams can triage and respond efficiently.
Key Values and Vision
- Innovation
- Security
- User-Centric Design
- Transparency
- Empowerment
Mission Statement
Our mission is to empower individuals and businesses by delivering secure, efficient, and user-friendly financial services.
Data Flow: From Network to Dashboard
Traffic is captured at the network edge, processed by sniffers/collectors, ingested through the API where detection and enrichment occur, and then stored in the website database for visualization and alerting.

Router / Probe
Routers or network taps mirror traffic to probes; these devices forward raw packets to local sniffers for inspection.

Sniffer / Collector
Collectors parse packets into structured events, enrich them (geo, DNS), and forward events to the ingestion API.

API Ingestion & Detection
The API receives events, applies detection rules and risk classification, then acknowledges and persists alerts for further analysis.
Database & Dashboard
Events and alerts are stored in the website database; dashboards provide charts, top attacked IPs, and filters to investigate incidents.
What IDSMS Provides
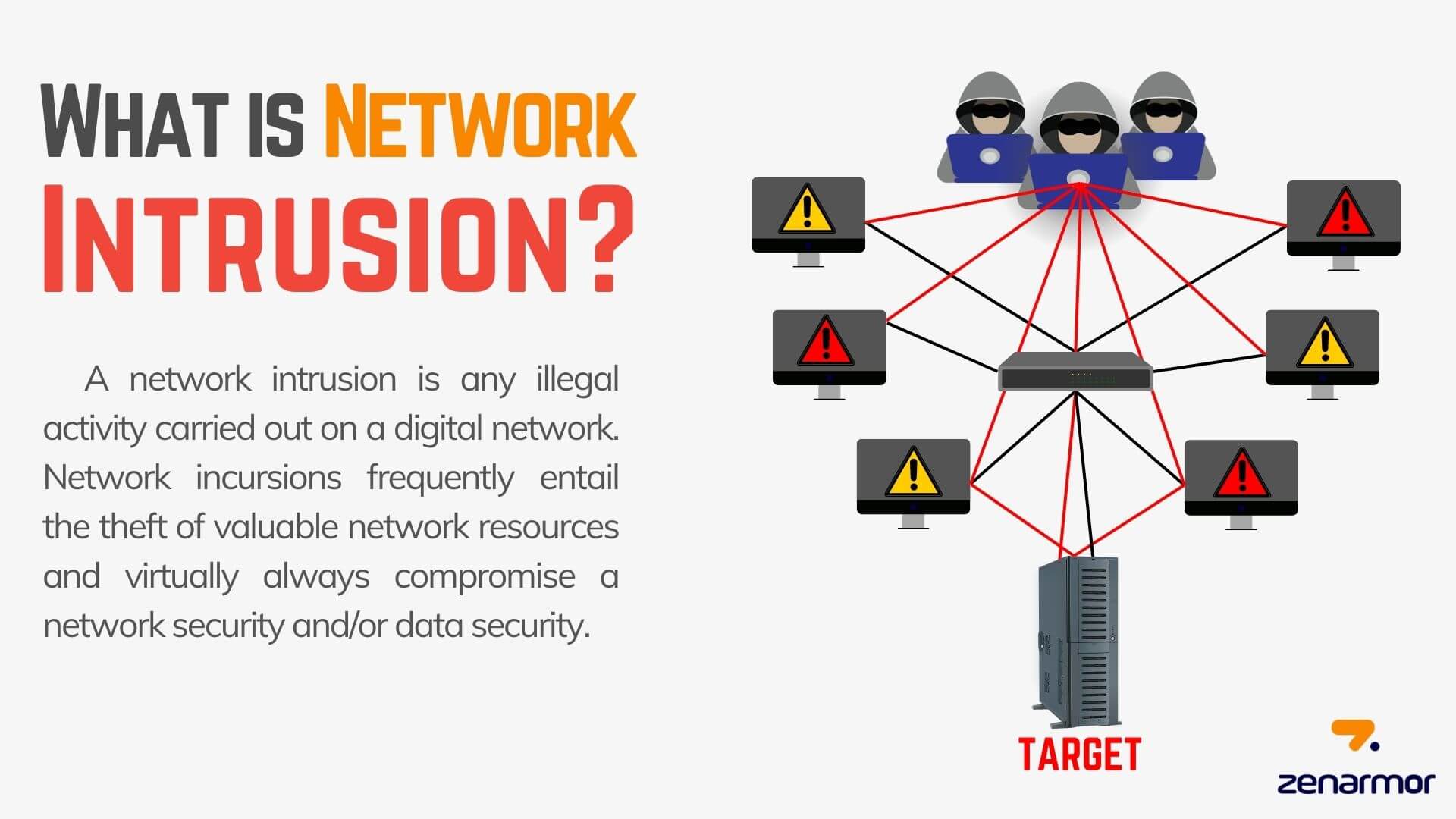
Real-time Intrusion Detection
Continuously analyze network traffic using signature and anomaly-based detection to surface suspicious activity in real time.
Alerting & Notifications
Configurable alert rules, multi-channel notifications (email, SMS, Slack), and escalation workflows to ensure fast response.
Comprehensive Logging
Capture and retain enriched event logs and packet metadata for forensic investigations and compliance with secure storage.
Dashboard & Analytics
Interactive dashboards with charts, top attacked hosts, timelines, and powerful filters for rapid triage and trend analysis.
Rule Management & Tuning
Create, test, and tune detection rules and suppression policies to reduce false positives and improve detection accuracy.
API & Integrations
REST ingestion and query APIs plus integrations for SIEM, ticketing systems, and threat intelligence feeds to fit existing workflows.
LOGIN ACCOUNT
